ALIEN INCLUSION
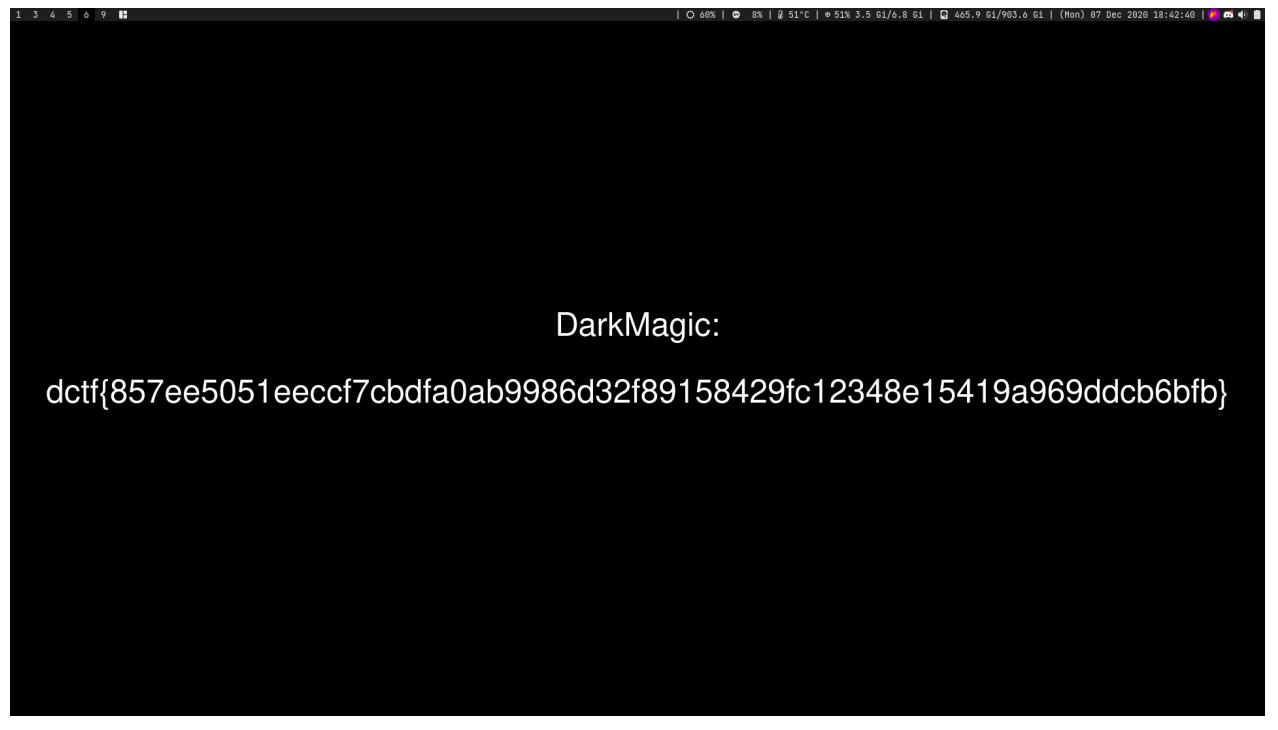
Proof of flag
FLAG = ctf{b513ef6d1a5735810bca608be42bda8ef28840ee458df4a3508d25e4b706134d}
Summary of the vulnerabilities identified
We can control which file we are includingg using the start post parameter and we can set it to the path of the flag.php file.
Proof of solving
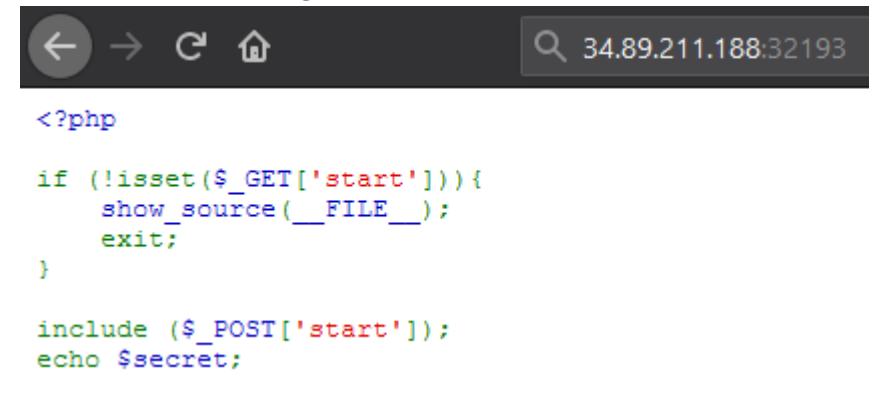
When we first access the page we are greeted by what seems to be the source code of the index.php file. Based on this source code, the name of the challenge and its description “Keep it local and you should be fine. The flag is in /var/www/html/flag.php.”, it is obvious we need to set the value of the “start” POST parameter to the absolute path of the flag and to also add a random value for the start GET parameter (also known as a query argument) in order to provent the exit on line 5 from ever being executed.