MODERN LOGIN Proof of flag
MODERN LOGIN Proof of flag
ctf{356c5e791de08610b8e9cb00a64d16c2cfc2be00b133fdfa5198420214909cc1}
Summary of the vulnerabilities identified
Challenge APK file can be easily decompiled using online services, scrolling through source files and assets we notice a mp3 which is not playable. Running file command on it we observe it is an archive, we decompress it and find obfuscated Python code. Cleaning up the code we start decoding the obfuscated strings in it and one of them is our flag.
Proof of solving
We begin by decompiling the challenge apk using a basic free online service.
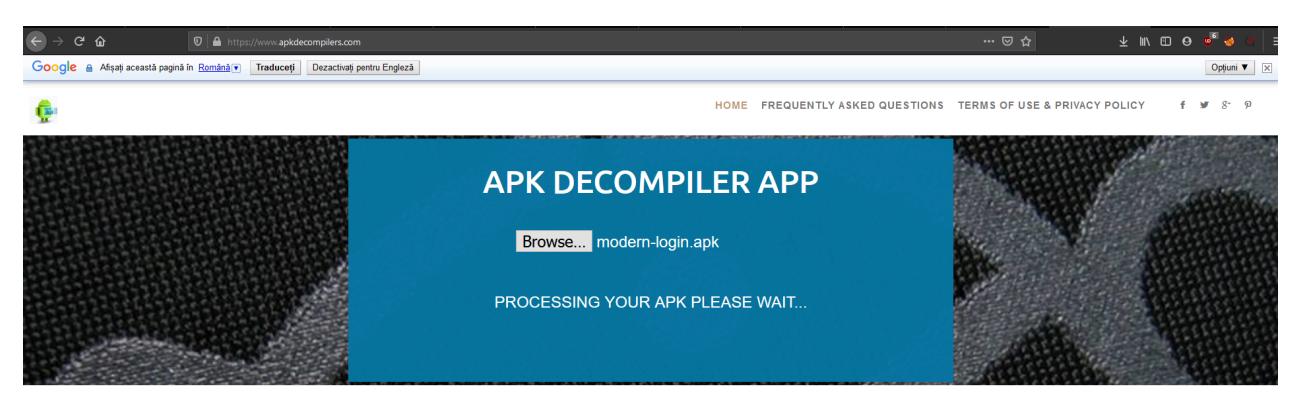
After downloading the resulting archive we can start looking through the source files, see what libraries are used etc. However that turned out to be a rabbit hole and we noticed that there is a single mp3 file in the assets folder which we thought was corrupted. But running the file command on it we find out it is actually a
sleshwave@DESKTOP-70BJVT3:/mnt/d/CTFs/dctf_2020/modern_login/assets file private.mp3
private.mp3: gzip compressed data, was "private.mp3", last modified: Wed Nov 4 14:28:05 2020, max compression
sleshwave@DESKTOP-70BJVT3:/mnt/d/CTFs/dctf_2020/modern_login/assets$
gzip archive.
After changing it to have a .gz extension we can use “gzip -d private.gz” to decompress it and find out that it contained only a tar file in it.
sleshwave@DESKTOP-70BJVT3:/mnt/d/CTFs/dctf_2020/modern_login/assets$ gzip -d pri^C
sleshwave@DESKTOP-70BJVT3:/mnt/d/CTFs/dctf_2020/modern_login/assets$ mv private.mp3 private.gz
sleshwave@DESKTOP-70BJVT3:/mnt/d/CTFs/dctf_2020/modern_login/assets$ gzip -d private.gz
sleshwave@DESKTOP-70BJVT3:/mnt/d/CTFs/dctf_2020/modern_login/assets$ ls -la
total 44884
drwxrwxrwx 1 sleshwave sleshwave 512 Dec 7 18:37 .
drwxrwxrwx 1 sleshwave sleshwave 512 Dec 5 19:40 ..
drwxrwxrwx 1 sleshwave sleshwave 512 Jan 1 1970 python bundle
-rwxrwxrwx 1 sleshwave sleshwave 2980 Dec 7 18:21 main.py
-rwxrwxrwx 1 sleshwave sleshwave 85 Nov 4 16:28 p4a_env_vars.txt
-rwxrwxrwx 1 sleshwave sleshwave 22978560 Dec 7 18:36 private
-rwxrwxrwx 1 sleshwave sleshwave 22978560 Dec 5 09:37 private.tar
-rwxrwxrwx 1 sleshwave sleshwave 98 Nov 4 16:28 sitecustomize.py
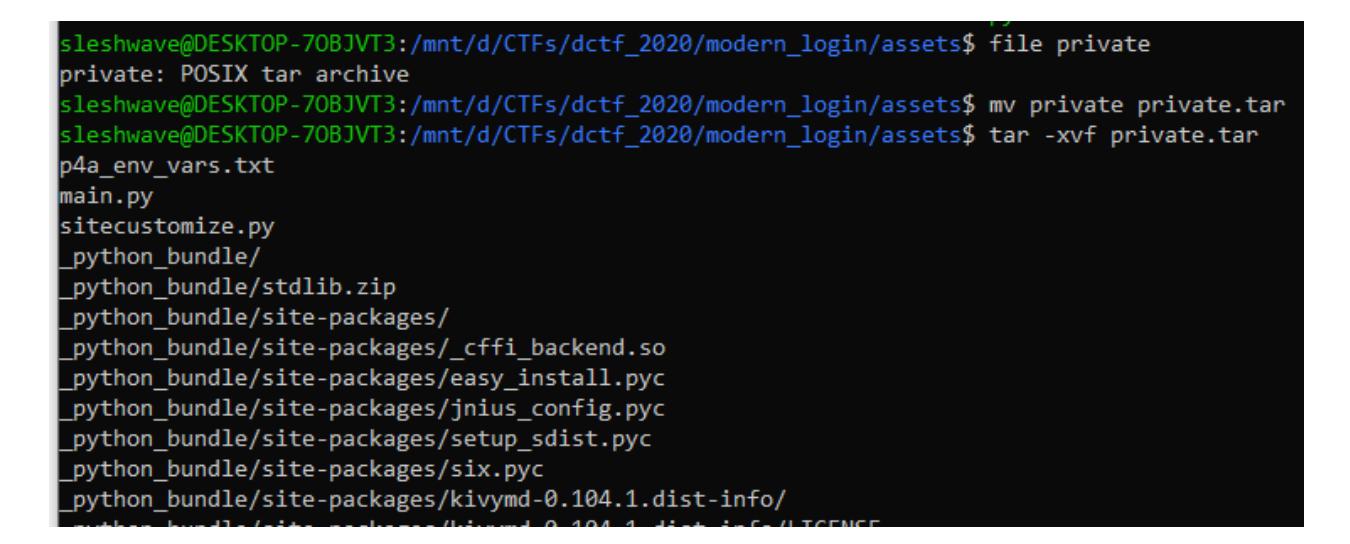
Now we are left with what seems to be a simple python project made for android with some dependencies. We can already tell we are interested only in the main.py file and maybe sitecustomize.py/p4a_env_vars.txt files but these last 2 turned out to be useless.
Looking through main.py we can see it is a heavily obfuscated file and that our first priority should be to deobfuscate it and make it run on our system (basically remove unnecessary
dependencies).
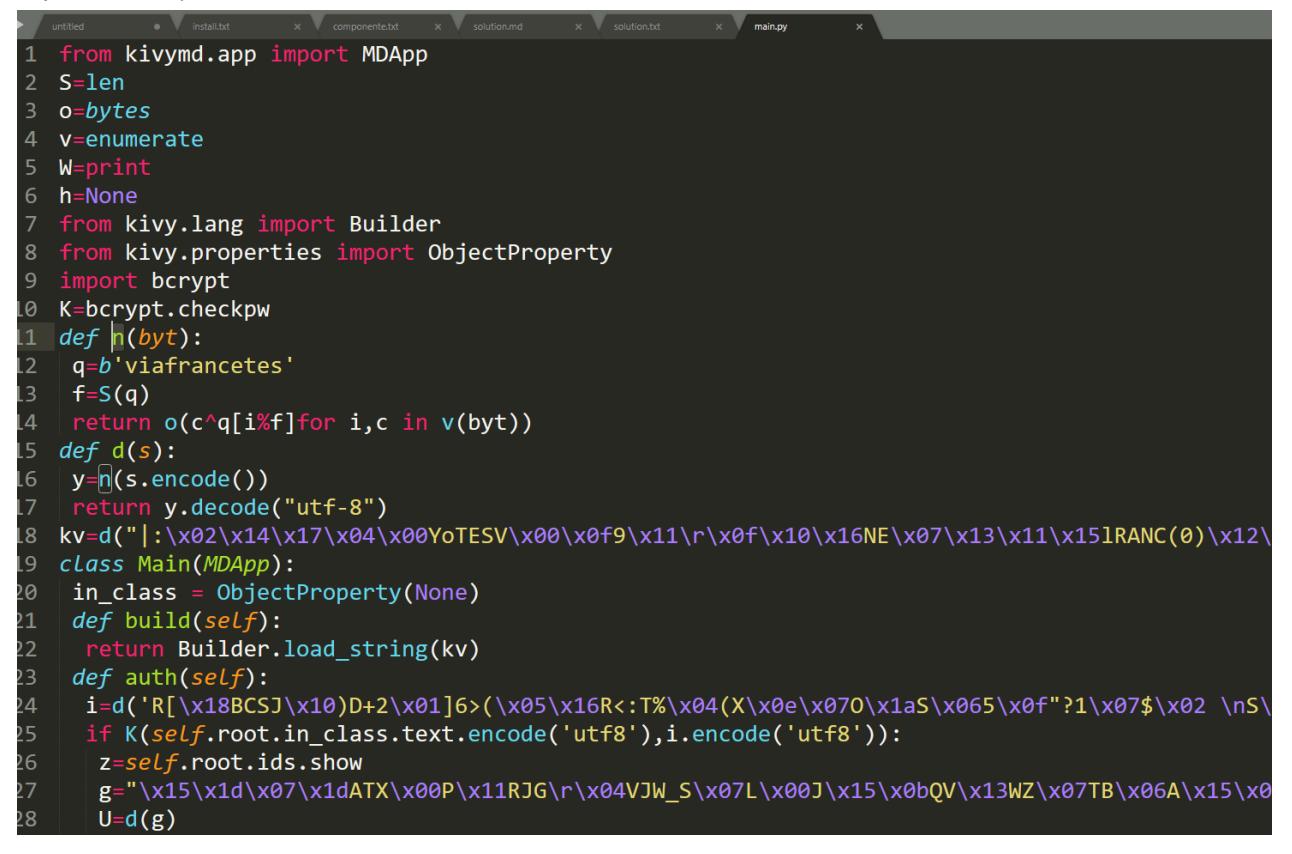
In order to deobfuscate it, we start by renaming variables and function names, cleaning up function calls. We then remove the unneeded imports, replace the functions. We also realise that there were some input fields that were used for changing the code flow (the if on line 25) and that the flag is stored in the g variable (its the one that gets printed if the “if” call is True). After all these steps the deobfuscated code looks something like this:
Running this deobfuscated code we get the flag.