QR-MANIA
QR-MANIA
Proof of flag
CTF{2b2e8580cdf35896d75bfc4b1bafff6ee90f6c525da3b9a26dd7726bf2171396}
Summary of the vulnerabilities identified
Inspecting the pcap file with wireshark I found HTTP responses with png images, each one containing a qr code, which decodes to a single character. The position of each character is inside the exif data of the corresponding image.
Proof of solving
Extract HTTP objects with wireshark from the provided .pcap file:
Among the extracted resources, the following .png files can be found:

Each one corresponds to a character in the flag
The order of the characters is contained in the EXIF data of the images
~/D/d/q/resources > exiftool *.png | xargs -n1 grep -i 'file name\|comment'
File Name : ajxxcwfgozxpbhnauore.png
Comment : 20/69
File Name : avudtreighimhcgmwape.png
Comment : 39/69
File Name : biuwfrwgdocdypyliqyt.png
Comment : 27/69
File Name : bynatxrryamhwwhmmroj.png
Comment : 46/69
File Name : cllzodvnyvvmbppaktsd.png
Comment : 44/69
File Name : czguxctbmqgfgxhvnwzr.png
Comment : 69/69
File Name : dfhwcysjjnrnhfziizlr.png
Comment : 56/69
File Name : dglakvmqmabxcqlpgbjb.png
Comment : 45/69
File Name : dhqclnghhlrjxjmhjzon.png
Comment : 54/69
File Name : dmdkaosivnyzxyzmglai.png
Comment : 65/69
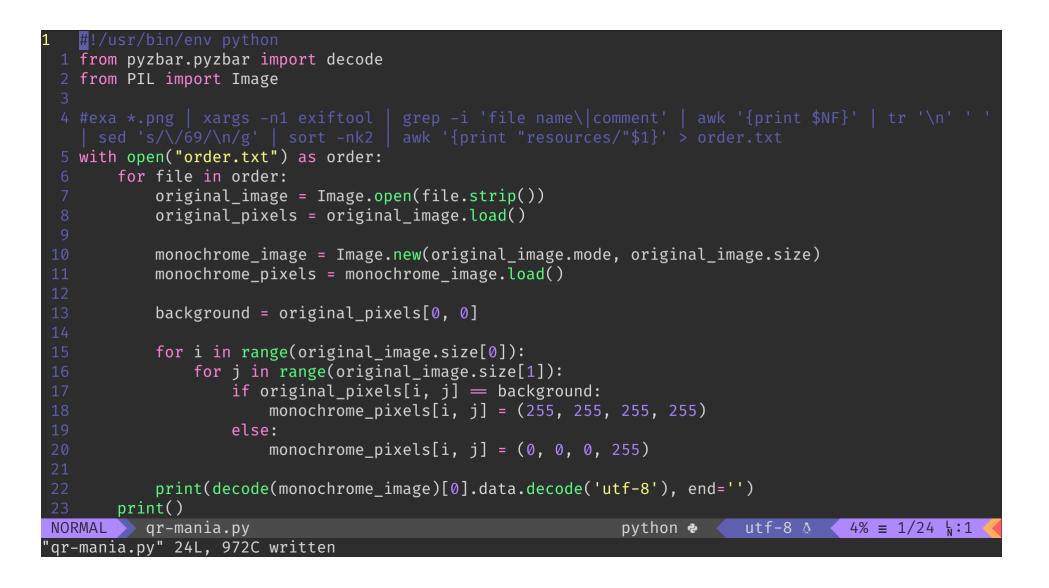
Convert the images into monochrome and decode them with the pyzbar library
Read other posts