YOPASS-GO
YOPASS-GO
Proof of flag
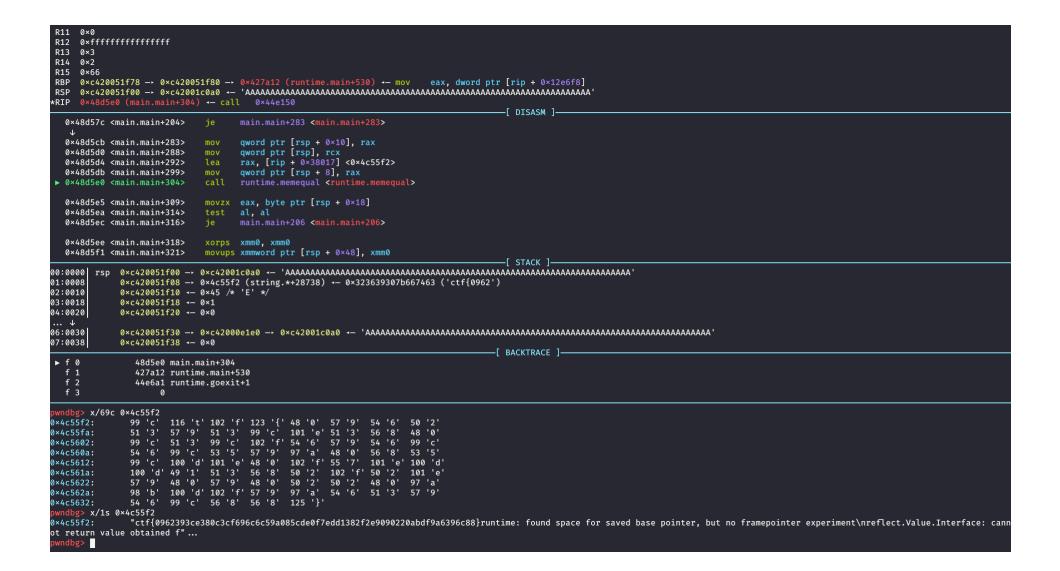
pwndbg> x/69c 0x4c55f2
0x4c55f2: 99 'c' 116 't' 102 'f' 123 '{' 48 '0' 57 '9' 54 '6' 50 '2'
0x4c55fa: 51 '3' 57 '9' 51 '3' 99 'c' 101 'e' 51 '3' 56 '8' 48 '0'
0x4c5602: 99 'c' 51 '3' 99 'c' 102 'f' 54 '6' 57 '9' 54 '6' 99 'c'
0x4c560a: 54 '6' 99 'c' 53 '5' 57 '9' 97 'a' 48 '0' 56 '8' 53 '5'
0x4c5612: 99 'c' 100 'd' 101 'e' 48 '0' 102 'f' 55 '7' 101 'e' 100 'd'
0x4c561a: 100 'd' 49 '1' 51 '3' 56 '8' 50 '2' 102 'f' 50 '2' 101 'e'
0x4c5622: 57 '9' 48 '0' 57 '9' 48 '0' 50 '2' 50 '2' 48 '0' 97 'a'
0x4c562a: 98 'b' 100 'd' 102 'f' 57 '9' 97 'a' 54 '6' 51 '3' 57 '9'
0x4c5632: 54 '6' 99 'c' 56 '8' 56 '8' 125 '}'
pwndbg> x/1s 0x4c55f2
0x4c55f2: "ctf{09052393ce380c3cf696c6c59a085cde0f7edd1382f2e90902200abdf9a6396c88"
ctf{0962393ce380c3cf696c6c59a085cde0f7edd1382f2e9090220abdf9a6396c88}
Summary of the vulnerabilities identified
Following the execution of the binary in gdb, I found a “memequal” call having as parameters the input string and the flag in memory.
Proof of solving
Follow the program execution until the “Scanln” call and input a random string
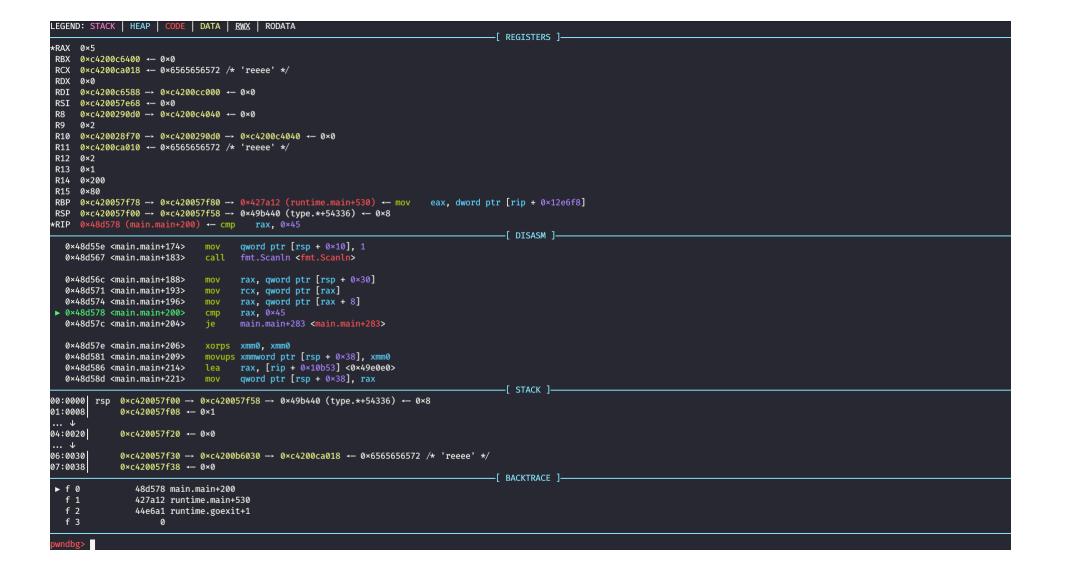
Right after the scanln call there is a length check, comparing the input string length with 69
Running the program again, this time with an input string of length 69, the execution eventually reaches a “memequal” call having as parameters the input string and the flag
Bx00000000000000000 10 in /home/lucian/Desktop/ctf/yopass.go
LEGEND: STACK HEAP CODE DATA BACK RODATA
TAX #* #* # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # <t< td=""></t<>
0+48572 cmin.main/2833 cmin.main/2835 trian.main/2835 0+485552 cmin.main/2835 cmin.main/2835 cmin.main/2835 0+485552 cmin.main/2835 cmin.main/2835 cmin.main/2835 0+485552 cmin.main/2835 cmin.main/2835 cmin.main/2835 0+485552 cmin.main/2835 cmin.main/2835 cmin.main/2835 0+485552 cmin.main/2835 cmin.main/2835 cmin.main/2835 0+485552 cmin.main/2835 cmin.main/2835 cmin.main/2835 0+485552 cmin.main/2835 cmin.main/2835 cmin.main/2835 0+485552 cmin.main/2835 cmin.main/2835 cmin.main/2835 0+485552 cmin.main/2835 cmin.main/2835 cmin.main/2835 0+485552 cmin.main/2835 cmin.main/2835 cmin.main/2835 0+485552 cmin.main/2835 cmin.main/2835 cmin.main/2835 0+485552 cmin.main/2835 cmin.main/2835 cmin.main/2835 0+485552 cmin.main/2835 cmin.main/2835 cmin.main/2835 0+485552 cmin.main/2835 cmin.main/2835 cmin.main/2835
0+4685[1] cmii.m.siin.321 moups nemerid (tr [rsp + +0k]), xmm8 [
↓
96:9281 → 9rc(x20851f38 → 9rc(x2081c080 → 9rc(x2081c080 ↔ 'AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
F € 4855e8 min.min+304
F 1 427a12 runtime.min+330
F 2 44e61 runtime.gooxit+1
F 3 € €
pundbg>
Print 69 characters from the obtained memory location
Read other posts