KALF GAME
#
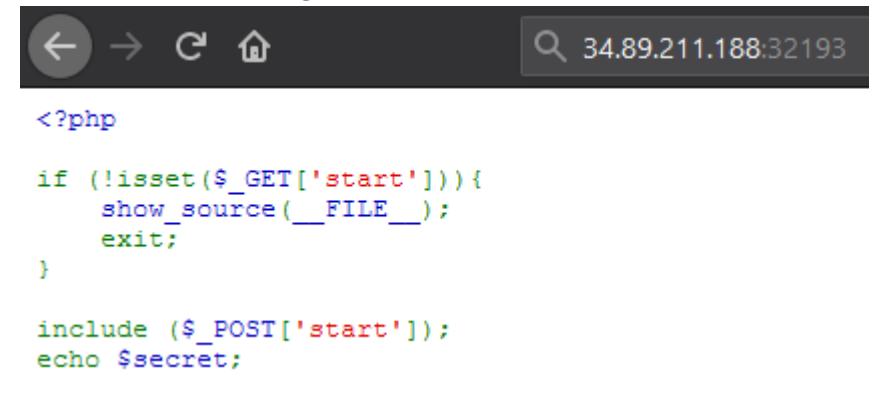
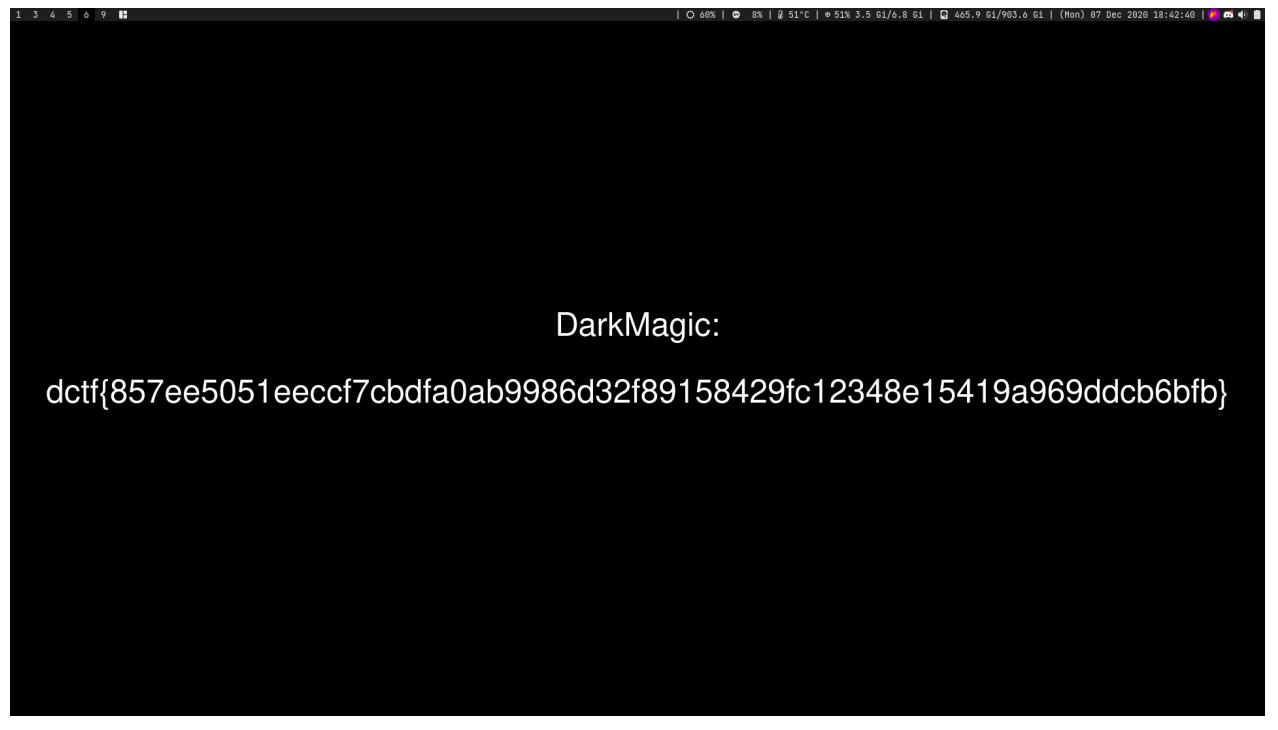
Proof of flag
#
01660706613050 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 00007061 000007061 00007061 00007061
Bodderfore:304-3] Cold XHF from from from SoftWork:34x3 () 0x560706423648 1.5 0x04111 SoftWork:31xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
msderodec3865f (dby)] 20 coderodec3865f (dby)] 20 coderodec3865f (dby)] 20 msderodec3865f (dby)] 21 msderodec3865f (dby)] 21 msderodec3865f (dby)] 21 msderodec3865f (dby) 21 msderodec3865f (dby) 21 msderodec3865f (dby) 21 msderodec3866f (dby) 21 msderodec3866f (dby) 21 msderodec3866f (dby) 21 msderodec3866f (dby) 21 msderodec3866f (dby) 21 msderodec3866f (dby) 21 msderodec3866f (dby) 21 msderodec3866f (dby) 21 msderodec386f (dby) 21 msderodec386f (dby) 21 msderodec386f (dby) 21 msderodec386f (dby) 21 msderodec386f (dby) 21 msderodec386f (dby) 21 msderodec386f (dby) 21 msderodec386f (dby) 21
0x560706c35072 [dbt] 0x560706c35072 [dbt] 0x560706c35072 (dbt] 0x560706c35072 488040377640. tea rax, [sym.care::ptr::drop_(n_place::h14b254b3868f5bb2] 0x560706c35092 48804c34083. tea rdx, [var_s607] 0x560706c35092 48804c34083. tea rdx, [var_s607] 0x560706c35092 6000 [m 0 000676c35685
0.569760:35685 [of:a]
; (OCS.3985 Trom from, from, 507.562786233867
scientifications: ebility jup exclamation ebility
:> dso ctf{ddba6614a32 hit breakpoint :>
ctf{ddba6614a32456631c125eb1a4327c52686c71d909a92ec05ea5eb510eae81d9}
Summary of the vulnerabilities identified
#
The game is a basic snake game(which is the best game of snake I ever played, thank you Lucian, you made my day happier) and hides the flag using strings that are stored on the stack and a cool function like rot13, and the best thing it was written in rust which is the best language so far for humanity.